The threat is mounting
According to Symantec’s 2018 Internet Security Threat Report, there has been a 13% overall increase in reported vulnerabilities since 2017. And what are you – an accountant, lawyer, chef, doctor or fighter pilot – supposed to do about it!? You didn’t sign up to be an expert in data security!
Well, that’s the problem we’re here to solve, folks. IT security is complex, but some of the biggest threats to your business can be solved by you today, because the solutions are found in good management practice, not technical know-how.
We’ve gone through each of these threats and sorted them in order from least resources, highest value to most resources, lowest value (where value is protecting your treasure and resources is time and/or money).
1. Your People
Your people are one of the biggest security threats to your business today. Yep. You trust them with your treasure and they hand it away – how could they?
Well, it’s not entirely their fault. In fact, once you know the solution, you’ll realise it’s more your fault than theirs.
Back to the fortress analogy. Imagine that software like Anti-Virus, Anti-Spam and Web Filtering are fences around the perimeter. They do a great job of stopping intruders from making it inside the compound, but what’s the point if your staff let them in the gate, walk them up the path and unlock the door?
Of course, they aren’t always doing this with any bad intent – it’s just that the best intruders wear disguises to make them seem friendly. This tactic is called “phishing” and is by far the most widely used infection vector, employed by 71% of malicious groups. Sophos’ Phish Threat Datasheet notes that “66% of malware is installed via malicious email attachments, and advanced spear phishing attacks cost business’ an average of $140,000 per incident”.
Solution: Staff Education
Resources: 2/10 | Value: 8/10
Cybersecurity education is absolutely critical for protecting your business’ data and it doesn’t need to be expensive.
The same internet that puts your business at risk is the internet that you can use to educate your staff. Websites like Coursera and Udemy provide numerous high quality, low-cost, self-guided IT Security courses for beginners.
- Udemy (FREE) – Cyber Security Course for Beginners 01
- Coursera ($63 AUD p/month) – Cybersecurity for Business Specialisation from the University of Colorado
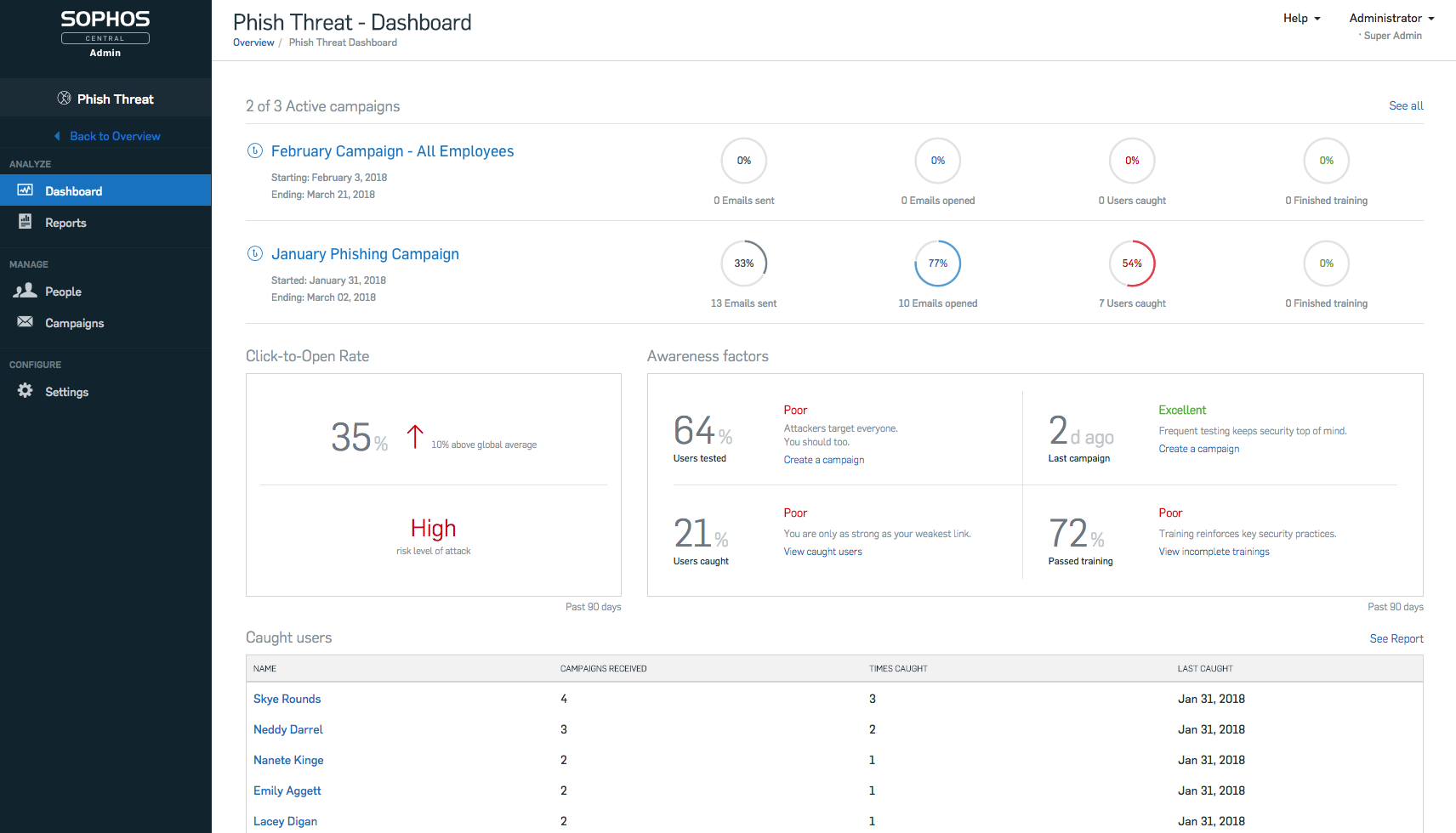
Once they’re trained up, check out Sophos’ Phish Threat. This product simulates phishing attacks by sending your people fake phishing emails and recording how they deal with them. You can then view detailed ‘user susceptibility’ analytics that shows how vulnerable your staff are, and help you tailor education to your business’ needs.
2. Outdated Software
As you sit back into your comfy red velvet chair, sipping fine wine next to a glowing fireplace, there’s a bloody, vicious battle raging just outside.
Intruders are scouring the walls of your fortress, looking for building defects and finding new ways to pick the locks, while software vendors are looking for the same vulnerabilities in the hope that they’ll find them first.
To give you some sense of the scale, Microsoft has released 194 security packs for Windows from the 1st of January 2018 to date. Each pack contains numerous individual fixes and updates to prevent intruders from getting in. Don’t believe me? Check out Microsoft’s cumulative list of Security Updates for Windows.
Don’t stand up too quickly (that wine will get to your head), but now you know. When was the last time you updated your computer? How many cracks are in the walls of your fortress?
Solution: Update Your Software
Resources: 3/10 | Value: 7/10
This is an obvious one but seldom do we come across businesses that are up-to-date (except our clients, of course). Whilst you should ensure that you keep all your software updated, here’s a list of some of the more common applications you should keep your eye on:
- Java
- Adobe Reader
- Adobe Flash
- Google Chrome
- Mozilla Firefox
Most important of all is Microsoft Windows itself.
If you’re a smaller business that manages it’s own IT, you can do this yourself right now. Here’s how:
For larger businesses, there may be more complexity, since Windows Updates (rarely) cause conflicts with custom or third-party software. If this is you, arrange a maintenance window with your Managed IT Service provider (who should really be doing this for you, anyway).
3. No Password Policy
Passwords are used to open the doors to your fortress’ vaults, and Password Policies determine the characteristics of your passwords; everything from how strong your passwords should be to how often they should be changed or whether the same password can be used twice. The list goes on.
In 2017, Preempt released their “Inspector Analysis” report which found that:
- 20% (1 in 5) of employee passwords can be easily compromised.
- 7% of employees are using compromised passwords.
- 13.39% of employees share their passwords with their colleagues.
These findings are of no surprise to us. When we first onboard a new client, there’s often no sign of a Password Policy (or it’s very poorly implemented).
When it does exist, there are usually exemptions; Directors who have decided that they’re too busy to reset their password every 30 days. As you can imagine, this is particularly problematic since senior people have access to far more business-critical information.
Solution: Set and Adhere to a Password Policy
Resources: 5/10 | Value: 7/10
If you can follow instructions, you can set a Password Policy. In our experience, the challenge here is not knowing how, but the change management piece that follows. This is because Password Policies impose effort on your people, and with effort comes frustration.
Not only will the Password Policy mandate that they regularly change their password, but they will need to think of a new one each time. Sure, it might be annoying – but not as annoying as losing all of your hard work in the blink of an eye.
To learn how to set basic Password Policies for your business, check out the video below.
To help you out, here is Microsoft’s Best Practice for each Policy:
- Enforce password history | Set to “24“
- Maximum password age| Set to “expire passwords between 60 and 90 days“
- Minimum password age | Set to “2“
- Minimum password length | Set to “8” (minimum)
- Password must meet complexity requirements | Set to “Enabled“
- Store passwords using reversible encryption | Set to “Disabled“
4. No IT Security Audits
Your business’ IT systems are really complex. They’re made up of tens of thousands of components and configurations – bricks in the walls of your fortress. Intruders only need one brick to have a crack or be slightly misplaced to get in. Just as you would get a building inspection to ensure the integrity of your walls, you should also audit your business’ IT systems.
“Yeah but, we’ve never had a security breach, and never will.”
How embarrassing it will be when you do. In 2016, Symantec reported that:
- 46% of attacks targeted small businesses (1 to 250 staff).
- 22% targeted medium businesses (251 to 2500 staff).
- 35% targeted enterprise businesses (2501+ staff).
In terms of their IT function, all of these business’ fall into one of three categories:
- Internal IT Function – They have an internal/in-house IT staff.
- Outsourced IT Function – They have outsourced IT to a Managed IT Service provider (like us!)
- No IT Function – They have neither internal or outsourced IT expertise.
No matter which category you fall into, your the walls of your fortress almost certainly has vulnerable bricks.
This is intuitive if your business has no IT function, but it actually applies to any business in any category. In-house IT teams or MSPs may have security-focused staff, but they aren’t security specialists who understand how security applies to every brick in every wall of your fortress.
Solution: Get an IT Security Audit
Resources: 7/10 | Value: 7/10
IT Security audits must be performed by IT security specialists, not your in-house IT people or outsourced IT provider. The firm you use will vary depending on where you’re from. This aside, here are some tips to get you started in the right direction:
- Discuss and explain the intent with your IT people before you look for a firm. Common-sense says this is good people management (let’s not unnecessarily threaten their jobs), but they may also be able to point you in the direction of a friend or colleague who is particularly skilled in this area.
- The IT security community can guide you. Look for IT Security Groups on Meetup.com (click here), attend the most popular groups and ask the organisers who they would recommend.
- Go to your network and seek their recommendations. You may already have people within your network who have engaged an IT security firm they have engaged and would recommend.
- Don’t select on cost alone. cheap audits only check the basics, and your business needs a thorough review.
Take the results back to your IT people. They will be able to provide you with some context and begin implementing recommendations. It’s critical to involve them in the process.

