We’ve diligently compiled and detailed 74 top cyber security best practices specifically tailored to Australian enterprises.
These best practices aren’t in any particular order. But they’re grouped by category to make it easy for you to hone in on the gold that’s most relevant to you.
Let’s dive in!
Table of Contents
- Endpoint Security
- Network Security
- Identity and Access Management
- Email Security
- Cloud Security
- Security Awareness Training
- Vulnerability Management
Get more insights like these
Receive advice from our industry-leading cyber security experts.
Tekspace will never send you spam or share your email address with a third-party.
Endpoint Security
1. Identify Your Endpoints
Start with categorising all your networks, from your desktops to mobile devices, based on importance and risk level. Having an up-to-date inventory can help guarantee that even the most critical devices have the most recent security measures in place.

2. Minimise Unnecessary IoT Devices
Limit the number of IoT devices that can access your organisation’s email systems. These devices usually lack strong security protocols, increasing the risk of a breach. Review the access policies to ensure only the necessary and secured work devices connect to the network.
3. Deploy Endpoint Detection and Response (EDR) Solutions
Use EDR solutions with threat detection and advanced analytics to monitor endpoint activities. Have your IT staff configure the software to send alerts for any suspicious behaviour. This is important so that they can investigate and remediate threats right away.
4. Consider a Managed Security Operations Centre (SOC)
If your organisation doesn’t have its own in-house SOC, consider the game-changing benefits of a Managed Security Operations Centre. Many of the major EDR/XDR providers offer this as a service that cannot only oversee your EDR agents but can also scale to monitor your full environment with Extended Detection and Response (XDR) capabilities.
This arrangement is perfect for those looking to achieve advanced, real-time threat detection and response without the complexity and cost of running an internal SOC.
5. Plan for Lost Devices
When an employee loses a work device, the IT team should quickly revoke access to sensitive accounts and data. If necessary, implement mobile device management tools to lock or wipe the lost device. The IT team should keep a list of recovery methods appropriate to the access method, like secondary temporary email addresses for one-time passcodes.
6. Strengthen Device Management in Microsoft Defender for Endpoint (MDE)
If you’re using MDE, you can utilise its built-in security controls to monitor and manage devices across your organisation. This enforces policy management to improve overall security for your entire network.
7. Monitor All Your Endpoint Activity Logs
Actively review logs on your endpoints to identify suspicious activities. Ongoing monitoring protects sensitive data and makes early threat detection easier.
8. Mandatory Scanning and Encryption for USB Storage Devices
To lock down your data security, implement two non-negotiable rules: always scan USB storage devices for threats and exclusively use company-issued, encrypted USBs. This dual approach not only spots potential malware before it infiltrates your network but also ensures that all stored data remains inaccessible to unauthorised users.
9. Implement Automated Patch Management
Automated patch management keeps your systems up to date, which lessens the risk of attackers exploiting vulnerabilities. This approach saves time for your IT team and makes sure the organisation follows industry regulations. You can also combine this process with a broader vulnerability management strategy to enhance security practices.
10. Harness Application Control
Application Control tools allow you to precisely manage which applications can operate on each endpoint. These effectively block unauthorised and potentially harmful software. By implementing Application Control, you’re not just enhancing security, you’re also taking a significant step towards meeting Essential 8’s mandates for mitigating cybersecurity threats.
11. Incorporate the Principle of Least Privilege (PoLP)
The Principle of Least Privilege (PoLP) is a cyber security approach that limits staff access to only what they need to complete their tasks. Furthermore, this principle limits user access to reduce the risk of security breaches.

12. Adopt a Zero Trust Approach
Zero Trust Network Access (ZTNA) should be a cornerstone of your cybersecurity strategy. Start by verifying every user and device attempting to connect to your network, regardless of their location. Implement strict access controls and least privilege principles to minimise exposure to risks. This approach not only secures sensitive data but also adapts to the evolving security landscape.
13. Implement a Bring Your Own Device Policy
It’s vital to implement clear usage and security requirements for employees who bring their own devices to work. This includes reviewing your BYOD policy and having mobile device management (MDM) tools to monitor them effectively.
Network Security
14. Use a Firewall (and keep it updated!)
Configure and maintain your firewall settings meticulously, keeping up with the latest security protocols and threats. Regularly update these settings to block unauthorised access and keep your network secure against emerging threats.
15. Execute a Comprehensive Network Audit
Conducting a thorough network audit is essential for identifying vulnerabilities and ensuring compliance with security standards. This process addresses possible weaknesses before criminals can exploit them.
16. Monitor Network Traffic
Make use of network monitor tools to regularly track your organisation’s devices or programs. Set up alerts for unusual activities so they can check for threats.
17. Utilise Security Information and Event Management (SIEM) Solutions
Make use of SIEM tools to collect and monitor security data in real time. This gives your security team a centralised view of any unusual activities or threats right away.
18. Embrace Secure Access Service Edge (SASE)
Introducing Secure Access Service Edge (SASE) into your network architecture is a transformative step towards streamlined and secure network operations.
SASE combines network and security functions with WAN capabilities to deliver comprehensive, dynamic, secure access. By consolidating these functionalities into a single, integrated service, SASE significantly simplifies management and enhances security across your entire network.
This approach not only reduces complexity but also scales protection as your organisation grows, ensuring that you maintain consistent security regardless of where users and devices are located. With SASE, you’re not just adapting to the evolving security landscape—you’re staying ahead of it.
19. Regularly Back Up Network Configurations
This practice is heavily important in the event of a cyber attack or human error. Have your IT department automate the backups and check them at least monthly.
20. Regular Penetration Testing
Regular penetration testing is essential to identify vulnerabilities in your network before attackers do. Schedule tests at least annually or after any significant changes to your IT environment. Use certified penetration testers to simulate realistic cyber attacks under controlled conditions. This proactive measure not only strengthens your security posture but also aligns with compliance requirements.

21. Restrict Physical Access to Critical Infrastructure
Use access controls or security badges, for instance, to limit access to sensitive areas inside your enterprise. This ensures that only staff who need to be there can get in, preventing unauthorised access.
22. Implement Logging and Monitoring Practices
Turn on logging and monitoring for all your network devices and keep an eye on user activity. This helps your team spot potential threats early and gather useful insights to boost your cyber security.
23. Establish a Guest Network
Set up a separate network for visitors to keep them away from your main systems. This protects your enterprise’s sensitive information and reduces the chances of outside cyber threats entering your network.
Identity and Access Management
24. Establish an Identity and Access Management (IAM) Solution
Set up a centralised IAM system to manage system, application and resource access easily across your organisation. This tightens the security of the enterprise and makes it simpler for every employee to know their access rights.
25. Implement Single Sign-On (SSO)
Use Single Sign-On to streamline employee access across multiple applications with one set of credentials. This simplifies the user experience, reduces the risk of weak passwords and improves security.
26. Use Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds extra security for your company. It asks for two or more ways to verify who is accessing the account. Even if someone knows your password, these extra steps can protect your data.

27. Implement Adaptive Multi-Factor Authentication (MFA)
Security shouldn’t be the same for everyone. Adaptive multi-factor authentication (MFA) changes how users log in based on several things, like their location or device. If someone tries to log in from an unusual location, they would need to provide additional verification.
28. Utilise Just-in-Time Access
Implement Just-in-Time Access to provide the staff with temporary access rights when needed. Only give employees access when needed to lower the risk of data breaches from unnecessary permissions.
29. Make Complicated Passphrases
It’s still important to make passwords hard to guess but easy to remember even though character composition isn’t required. Just as Microsoft recommends, aim for at least 14 characters and avoid common passwords or phrases. Also, it’s best not to reuse passwords used outside work or other websites.
30. Have the IT Department Monitor and Log User Activities
Get your IT team to actively monitor and log employee activities. This approach will help your staff to proactively investigate any suspicious behaviour.
31. Monitor for Suspicious Login Attempts
Investigate unusual login attempts to keep your organisation safe from potential breaches. If the IT team sees suspicious email login attempts, they should quickly check where the attempts came from. They should immediately reset the passwords for the affected accounts.
32. Map the Enterprise’s Workforce to Assign Privileges
Map out the staff to assign appropriate access privileges based on their roles. This ensures that only they have access to the resources necessary for their job functions.
33. Review Employee Access Rights Regularly
Review user privileges every few months to see who still needs access. This keeps your data safe and allows everyone in the enterprise to only have the access they need for their job.
34. Have a Structured Onboarding Process
The IT and HR departments should work together to create an onboarding process for new employees’ access from day one. This process prevents delays and grants necessary permissions.
35. Have a Clear Offboarding Process
Create an offboarding process to revoke access from any staff who left the enterprise. Regular account management audits are important for protecting sensitive information and maintaining overall security.
Get more insights like these
Receive advice from our industry-leading cyber security experts.
Tekspace will never send you spam or share your email address with a third-party.
Email Security
36. Implement Strong Access Controls
Having solid access controls for your email security strategy can protect email accounts and sensitive information. These practices include having a strong password, using multi-factor authentication, leveraging single sign-on and locking an account after multiple failed login attempts. It is also important to restrict access for staff depending on their job role.
37. Keep Software Updated
Make sure you keep your email clients, servers and other software updated with the latest security patches to stay one step ahead of any vulnerabilities. It’s a good idea to keep an inventory of all the software, email clients and servers you use, so you know what needs attention.
Also, establish a patch management policy that prioritises critical updates. Review and conduct security patches to make sure everything is up-to-date and complies with the enterprise’s patch management policy.
38. Use Email Encryption Tools
Have the IT staff use email encryption tools to protect sensitive data. These tools scramble the content of emails, making them unreadable to unintended people. As a result, only authorised recipients can access confidential emails.

39. Deploy Email Content Filters
An email content filter scans emails for malicious content before they reach your network. Ask your IT team to customise these filters to flag specific threats relevant to your business environment.
40. Thorough Security Awareness Training
Educating staff can create a strong defence against threats online. Security Awareness Training involves continuous training and simulations. You should also review the risk analysis figures to determine the effectiveness of your training.
41. Use Email Monitoring Tools
Utilise email monitoring tools to keep watch on anomaly behaviour in your organisation’s email traffic. Configure these solutions to alert you to any suspicious activity detected so that the IT team can take action and mitigate risks.
42. Apply a Data Loss Prevention (DLP) Policy on Emails
Direct the IT team to implement a DLP policy to secure valuable data in emails. This helps stop both accidental and intentional leaks that could harm your organisation’s reputation. Some of the more mature API Email Security solutions also have DLP capabilities!
43. Utilise Email Verification Protocols
Make use of email verification protocols to make sure of the authenticity of the email messages. DomainKeys Identified Mail (DKIM) adds a unique signature that prevents tampering. Sender Policy Framework (SPF) verifies that only authorised servers can send emails on your behalf, reducing the risk of phishing and spam attacks. Domain-based Message Authentication, Reporting and Conformance (DMARC) checks SPF and DKIM records to make sure you only receive genuine email messages.
44. Implement API Email Security
An API-based email security solution provides seamless integration with your email platform, adding an extra layer of protection against phishing, malware, and spam. Unlike traditional gateway solutions, API-based security works within the platform to detect threats faster and more accurately. It can also provide real-time insights and automated responses to suspicious activities. This advanced approach keeps your email communication secure without disrupting the user experience.
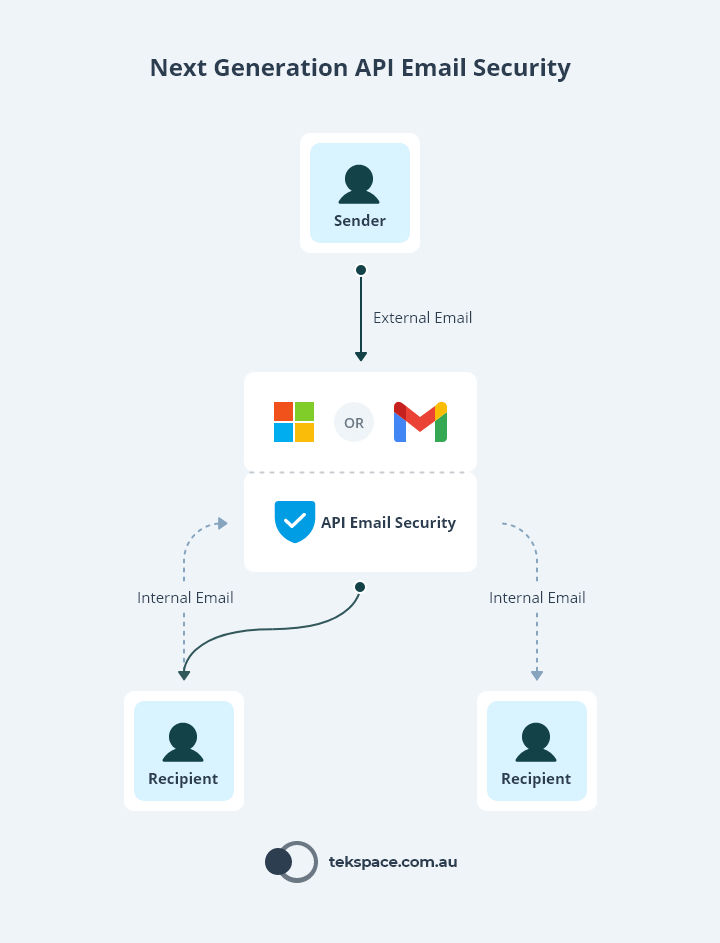
45. Review Third-Party App Access
Regularly assess the third-party applications that have access to your email systems. This practice helps make sure that only trusted services interact with your data, reducing the risk of breaches. Engage your IT team to establish a review schedule and maintain a secure environment.
46. Disable Auto-Download for Attachments
Direct the IT team to disable the auto-download feature in email settings across the organisation. This security practice helps block possible viruses, malware and even spyware from infiltrating work devices.
47. Don’t Access Email Over Unsecured Wi-Fi Networks
Educate the staff about the risks of using public or unsecured Wi-Fi networks. Encourage them to use a secure connection or VPN to protect their emails. It’s a good idea to remind them that staying safe online helps keep the entire organisation secure.

Cloud Security
48. Implement a Runtime Cloud Native Application Protection Platform (CNAPP)
Implement a runtime CNAPP to achieve comprehensive visibility and control across your cloud environments. These platforms combine all the capabilities of traditionally separate solutions (CSPM, CDR, CWPP, etc.) into a single pane of glass.
Importantly, leading CNAPPs will work at runtime (i.e., real time) to scan your cloud configurations, networks and applications, pinpointing misconfigurations and compliance issues before they escalate into threats. Using a CNAPP strengthens your security posture with a solution tailored to the dynamic nature of cloud computing.

49. Set Up Continuous Monitoring and Logging
Track system changes and user activity using real-time analytics. Your IT team can use tools to identify suspicious behaviour and quickly identify and address security risks. Again, a CNAPP can do this, too.

50. Apply Cloud Encryption
Ensure you’re using a public cloud provider that encrypts your data at rest and in transit. If you’ve built your own cloud, you’ll need to implement this yourself.
51. Adopt DevSecOps
DevSecOps is crucial for embedding security at every stage of your software development lifecycle. Start by incorporating automated security tools that can scan code for vulnerabilities in real time as developers write it. Foster a culture where security and development teams collaborate closely, sharing responsibilities and insights to preemptively address security issues. This integration not only speeds up the deployment process but also significantly reduces the risk of security breaches in your final product.
52. Implement API Security
API security solutions are essential for protecting against vulnerabilities inherent in your software’s interfaces. These tools monitor and manage the traffic flowing through your APIs, detecting and blocking malicious activities and data breaches. Implement solutions that offer comprehensive analytics to understand API usage patterns and identify anomalies early. Of course, mature CNAPP solutions can do this for you, too.
53. Monitor Cloud Configurations
Check your cloud setup regularly for misconfigurations. The IT team should run audits and use automated tools to fix any issues. This prevents vulnerabilities before they become serious threats. Again, mature CNAPP solutions can do this for you, too.
54. Use Cloud Security Posture Management (CSPM)
Deploy CSPM tools to monitor any misconfigurations, unintentional exposure or compliance risks in a continuous way. Your IT team can automate compliance checks and fix security gaps across all cloud infrastructures. Note that CSPM is part of a mature CNAPP solution.
55. Use Data Classification Tools
Identify and classify all the sensitive data in your cloud using specific tools. Get your IT team to implement this to handle data properly. It treats confidential information with extra care.
Security Awareness Training
56. Create a Cyber Security Awareness Program
Establish a comprehensive cyber security awareness program for all employees. This program should educate staff about the latest cyber threats and how to recognise them. By fostering a culture of security awareness, you empower your team to make informed decisions and protect your organisation’s assets.
57. Phishing Simulations
Phishing simulations are a great way to test how the staff handles these types of attack. This will help you pinpoint your enterprise’s vulnerabilities and adjust your training sessions for a stronger defence.
Also, use a variety of phishing simulations, like link phishing, attachment phishing and data entry phishing. Each type targets specific actions, such as getting a user to click a link or enter information on a landing page.
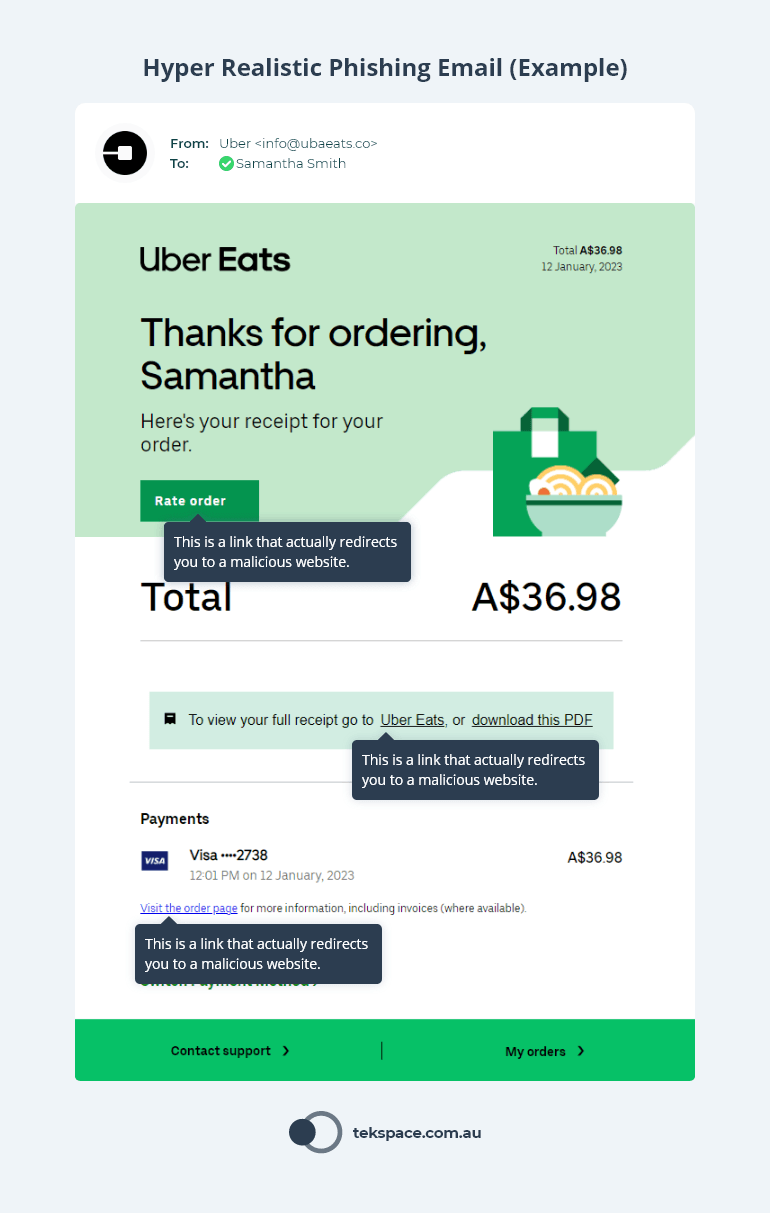
58. Benchmark Staff with the Same Simulation Template
Benchmark your staff with the same phishing simulation as a baseline. From there, you can assess their ability to deal with these scenarios, and you can track improvements that may require further training.
59. Encourage the Habit of Reporting Suspicious Emails
Include report phishing features in your training so the staff can develop a more proactive approach to emails they receive. This continuous habit lets them be more wary of downloading attachments or clicking links.
60. Incorporate Different Simulations
Phishing simulations can take the form of realistic emails that mimic well-known brands or simple but tricky text-based HR emails. Either way, the simulation should be something that the staff would likely engage in.
61. Utilise AI and Machine Learning
Sending the same email is great as a benchmark but can disengage people in the long run. AI and machine learning can adjust simulations based on the assessed susceptibility traits of each staff.
62. Security Training Programs Should be Concise and Continuous
Keep your training programs concise, frequent and spaced out over a long period of time. Consistent cyber security training helps the staff retain more information. This commitment to continuous learning forms a proactive security culture within your enterprise.
63. Create Personalised Learning Approaches
Every individual is unique, including their learning preferences. It’s best practice to adjust the training using different forms (visual, aural, reading/writing, kinaesthetic).
64. Include a Report Phishing Button
Include a report button for employees to click if they notice suspicious emails. If the email is in a simulation, users should receive positive feedback for identifying it correctly. If not, inform the staff that the email could be harmful and to notify IT about it.
65. Handle Reported Phishing Emails
IT professionals with cyber security expertise should review the reported emails to confirm if they’re genuine phishing. The training platform should include a workflow for detecting whether an email is safe and the necessary actions.
66. Utilise an Automated Training Platform
Use automated platforms to reduce manual efforts and have a more seamless process during the training. Choose a platform that automatically delivers customised phishing simulations and training content on a set schedule.
67. Integrate Staff Onboarding and Offboarding Processes
Make sure that the newly onboarded staff is in your security awareness training program. The IT team should integrate the training software with the identity provider (Microsoft Active Directory or Google Workspace). When a member of staff leaves and their account is deactivated in your user provisioning system, it will also be deactivated in your Security Awareness Training (SAT) software.
68. Create Role-Specific Training Modules
Develop training modules personalised to the specific roles within your organisation. Each module should address specific security challenges for different departments. This training helps employees understand their role in keeping the organisation safe and compliant.
69. Monitor Training Effectiveness
Use analytics tools to assess the effectiveness of your training programs. Tracking metrics like completion rates, staff feedback and quiz scores help identify areas for improvement.
Vulnerability Management
70. Consider Essential 8 Compliance for App and OS Patching
Staying ahead of threats means getting serious about your application and OS patching—core components of the Essential 8. Set up a bulletproof patch management system that regularly checks and swiftly applies updates.
Workshop: ML3 for App and OS Patching (on Auto-Pilot)
Focus on the urgent patches first by evaluating how vulnerabilities might impact your specific system setup. Better yet, automate this process to keep your defenses robust without missing a beat. This proactive approach doesn’t just boost security—it aligns perfectly with top-tier cybersecurity practices.
71. Real-Time Vulnerability Detection Across Platforms
Implement a vulnerability management approach that continuously monitors for security gaps across all major operating systems, such as Windows, Mac and Linux. This enables your team to detect vulnerabilities as soon as they appear, enhancing your ability to respond quickly and effectively.
72. Context-Aware Vulnerability Prioritisation
Prioritise vulnerabilities not only based on their severity ratings but also by considering the specific context of your environment. For instance, a vulnerability with a high severity rating might be less critical if it exists on a secured, non-internet-connected server. Adjusting the criticality based on context helps focus efforts on the most impactful issues.
73. Smart Vulnerability Remediation Strategies
Develop smart rules and automation for the remediation process to streamline and secure your systems efficiently. Automate the remediation of low-risk software vulnerabilities to free up resources for manual review and intervention on more complex and less understood software issues.
74. Patchless Protection for ‘Unpatchable’ Vulnerabilities
Employ a mature vulnerability management platform that allows you to protect against vulnerabilities for which no software vendor patch is available. This proactive security measure ensures that even without an official fix, your system remains secure against potential exploits.
Conclusion
A business is at risk if there are no implemented cyber security practices in the workplace. Performing these best practices not only safeguards the enterprise’s data but also that of the customer’s.
Get more insights like these
Receive advice from our industry-leading cyber security experts.
Tekspace will never send you spam or share your email address with a third-party.





