Are your cyber security misconceptions putting your business at risk?
The cyber security landscape is constantly changing, so it’s more important than ever to know what’s true and what’s not.
That’s why we’re here to tell fact from fiction when it comes to the most common cyber security myths and misconceptions.
Let’s dive in.
1. Cyber security is an ‘IT department’ issue
Many people believe that cyber security is solely the responsibility of IT departments.
And in some ways, it’s true.
IT departments do have a responsibility to ensure that their organisation is well positioned to defend against malicious attacks. There are a plethora of cyber security protections that IT departments should have in place.
But no product, system or configuration is perfect. Which means that sometimes, attacks can slip through the cracks.
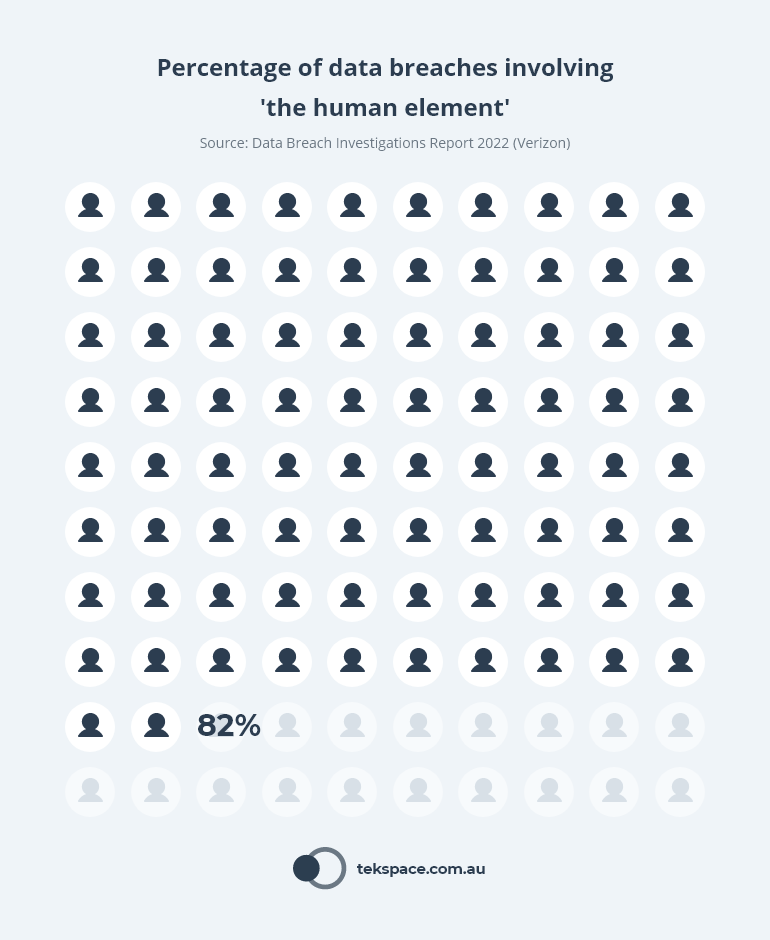
And when you consider that in 2022, 82% of all data breaches involved the ‘human element’ (phishing, stolen credentials etc.), it becomes clear that we all have a role to play in protecting our organisations – especially if IT are already doing the best they can.
2. Small businesses are not targeted
Many people believe that only large businesses with huge revenue are of interest to bad actors.
And while this sounds rational, it’s not even close to reality.
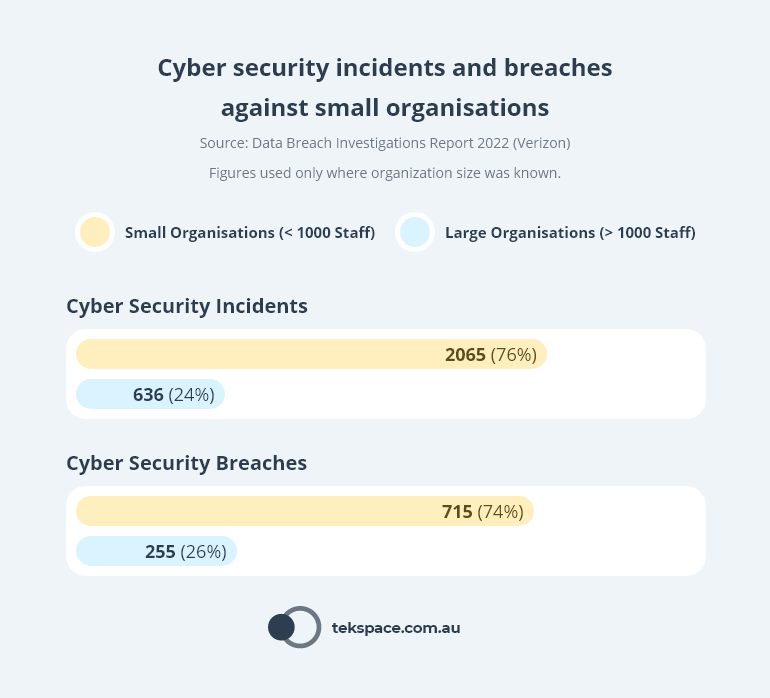
Recent research from Verizon shows that approximately 25% of all cyber security incidents and breaches are launched against businesses with less than 1000 staff.
Why are small businesses the target?
So why are small businesses are targeted more than large businesses?
Well, we think there are two reasons.
Firstly, small businesses tend to invest less in cyber security leaving them more open to attack. Breaches of larger businesses typically result in bigger amounts of stolen money or compromised records, but there are fewer instances of breaches involving larger businesses than smaller ones.
Secondly, most modern attacks are carried out autonomously and at massive scale. Perhaps this points to another misconception, which is that breaches aren’t carried out by people who sit behind a computer and tap away at the keyboard in real time. Code does the heavy lifting, and humans get involved much later.
Get more insights like these
Receive advice from our industry-leading cyber security experts.
Tekspace will never send you spam or share your email address with a third-party.
3. Security software is enough
Security software is critical and, just with most things, there are clear leaders and followers in each product category.
But security software is only one part of a robust security strategy.
Why?
Because security software is added on top of your existing IT infrastructure, and is usually designed to protect one specific aspect of it. It has no influence over the way your IT infrastructure is designed and configured.
For example, every car has safety features like airbags and seat belts – and they are incredibly important for road safety.
But if the engineers have not designed crumple zones or reinforced the chassis – or if the driver hasn’t had lessons – then the passengers are at significant risk in the event of an accident, regardless of whether airbags or seat belts are installed.
Secure your underlying IT infrastructure
So, how can you ensure your IT infrastructure is ready for the next cyber security incident?
- Ensure staff have adequate cyber security knowledge with continuous security awareness training. It should have automated phishing simulations and a pre-built curriculum of lessons spanning numerous topics.
- Implement ‘zero trust’ user permissions and access control. This is where access and control over your your IT systems is denied, unless explicitly required.
- Ensure all operating systems, software and hardware firmware is regularly updated. If you’re following the Essential 8 framework, even Maturity Level 1 (the lowest level of compliance) requires that updates are applied within 2 weeks, or 48 hours if there is a known exploit.
- Disable Microsoft Office macros across all user accounts. These macros can contain malicious code, resulting in bad actors gaining access to sensitive information.
- Enable regular and automated backups of all business data. Ideally, the backup system is contained within it’s own network and frequently tested (for context, we do this daily). Reliable backups are critical to ensuring you can restore systems or data in the event of a breach.
- Enforce a strong password policy to ensure that your organisation can resist common attacks and contain attacks (i.e.: prevent them from spreading) should they occur. Check out Microsoft’s Password Policy Recommendations for guidance.
4. Strong passwords are sufficient
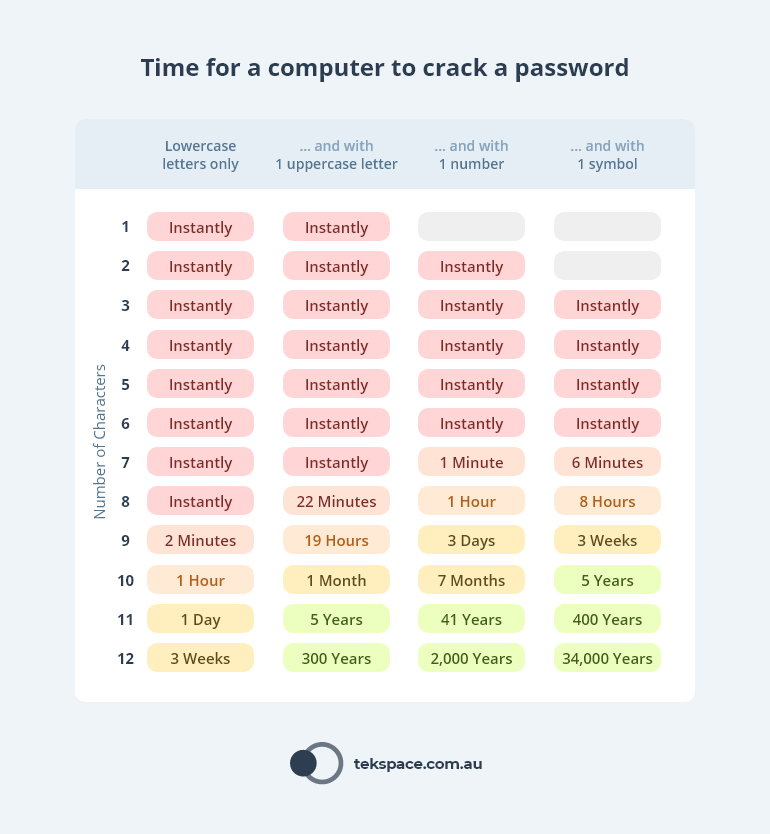
Strong passwords are important. In fact, recent research into password strength shows that difference between having your password cracked in 2 minutes and 34000 years is just 3 extra characters.
But password strength alone is not enough to ensure effective cyber security.
Passwords can be guessed, stolen or cracked, and once one password is breached, it could lead to a domino effect where multiple accounts are compromised.
Implement Multi-factor Authentication (MFA)
This is where multi-factor authentication (MFA) and password managers come in.
MFA adds an extra layer of protection by requiring users to provide additional credentials beyond just a password, such as a fingerprint, a security token or a one-time code.
This means that even if someone knows or guesses your password, they won’t be able to access your account without the additional credentials.
According to Google, enabling multi-factor authentication can prevent up to 99.9% of account takeovers.
Deploy password managers
Password managers, on the other hand, are tools that generate and store complex, unique passwords for each account.
This means that users don’t have to remember multiple passwords, which can lead to the use of weak, easily guessable passwords.
Password managers also help prevent phishing attacks, as users don’t have to enter their passwords manually on potentially malicious websites.
5. Cyber security is too expensive
Whilst many organisations acknowledge the importance of cyber security, they also struggle with the increase to their IT budget (or that a new cyber security budget needs to be allocated).
Executives in particular see costs going up but revenue staying flat, so the hesitance is entirely warranted.
That is, until you paint a picture of the alternative.
How much do data breaches cost?
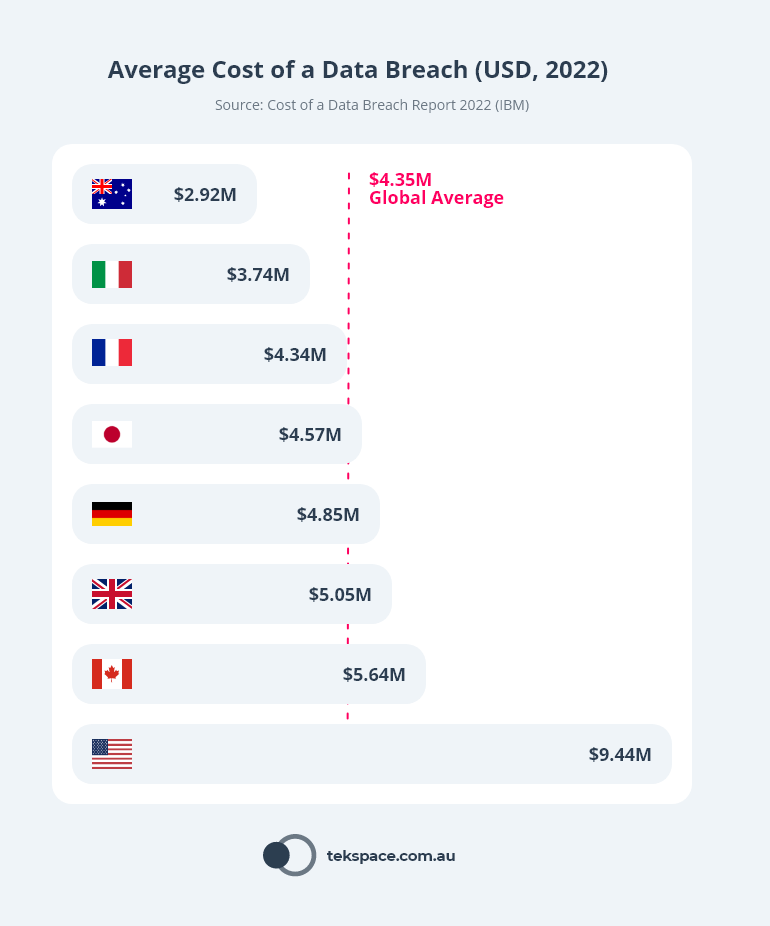
IBM’s ‘Cost of a Data Breach Report’ showed that in 2022, the global average cost of a data breach was $4.35M USD (approx. $6.5M AUD).
It also showed that in the same year, 83% of organisations that had a breach experienced more than one.
So while cyber security initiatives do increase costs, they also help to minimise (or even eliminate) the loss of hard-earned revenue.
6. Cyber attacks only come from external sources
Another common misconception is that cyber attacks only come from shady hackers hiding in the darkest corners of the internet.
But sometimes, even the people who work within a company can be a danger to its security.
These “insider threats” can be just as harmful as outside hackers, if not more so. This is because the people who work for a company often have access to sensitive information and systems, making it easier for them to cause damage if they want to.
According to a report by Verizon, insider threats were responsible for 22% of data breaches in 2021. Additionally, the same report found that financial gain was the most common motivator for insider threats, accounting for 86% of incidents.
So, what can we do to protect ourselves from these inside threats?
Educate staff about cyber security
First, it’s important to teach everyone in the company about cybersecurity risks and how to spot potential problems. This way, employees will know what to look out for and can help keep the company safe.
Limit access to important information
Next, it’s a good idea to limit who has access to important information.
By only giving access to the people who really need it, there’s less chance of someone accidentally (or intentionally) causing a security issue.
Have a cyber security incident plan
Finally, it’s essential to have a plan in place for what to do if something does go wrong.
This should cover both outside attacks and insider threats, so the company can quickly respond and limit any damage that might happen.
Get more insights like these
Receive advice from our industry-leading cyber security experts.
Tekspace will never send you spam or share your email address with a third-party.
7. All cyber attacks can be prevented
While it is a common belief that all cyber attacks can be prevented with the right security measures in place, the truth is that no organisation can be entirely immune to cyber threats.
The rapidly evolving nature of these threats, combined with the increasing sophistication of cyber-criminals, makes it challenging to guarantee absolute protection.
By implementing a proactive strategy and taking specific measures, organisations can minimise the impact of cyber attacks and recover more efficiently.
Create and (regularly) update an incident response plan
Establishing a clear plan that outlines how your organisation will respond to security incidents, including assigning roles and responsibilities, communication protocols, and recovery procedures.
Then, conduct periodic reviews and incorporate lessons learned from previous incidents to refine the plan and improve its effectiveness.
Notably, recent cyber security research from the Australian Government shows that while 79% of Australian organisations have an Incident Response Plan, only 49% of them test the plan at least once every 2 years.
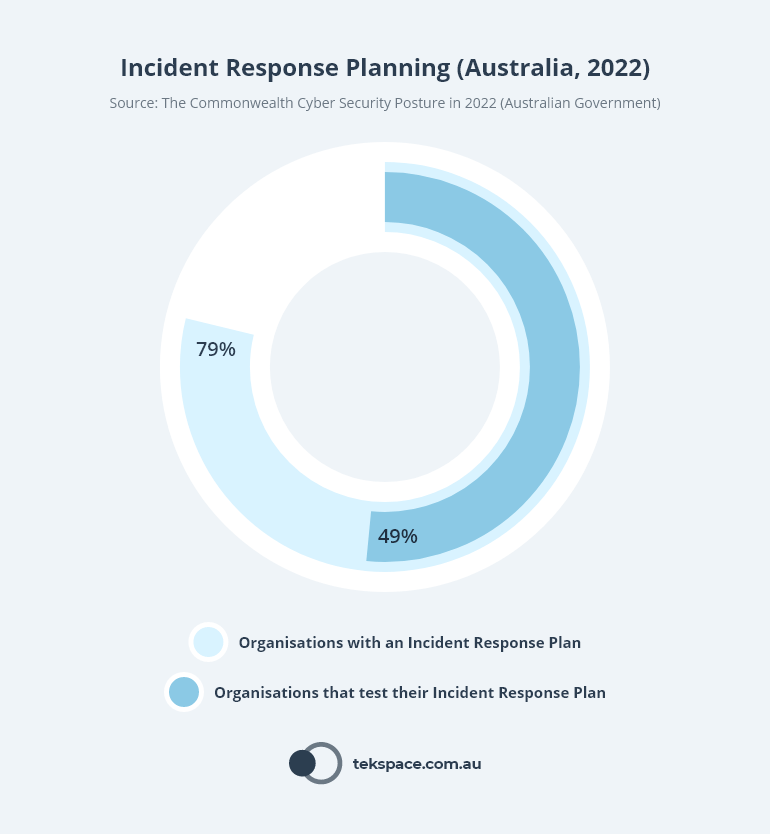
Implement a robust data backup strategy
Protect critical information and ensure it’s availability in the event of an attack by implementing backup, including off-site storage with multiple copies.
Regularly test backup systems to verify their effectiveness and reliability.
Collaborate with external partners
Establish relationships with external partners, such as law enforcement, cybersecurity experts, and industry associations, to share information about threats and best practices. This collaboration can provide valuable insights and support during a cyber attack.
8. Cyber Security is a one-time effort
A common misconception is that cybersecurity is a one-time effort, where implementing a set of security measures will provide lasting protection.
In reality, cybersecurity is an ongoing process that requires constant vigilance, updates, and adjustments to stay ahead of evolving threats and maintain a strong security posture.
So, assuming you’re on-board with on-going change, how do you bring your colleagues on the journey with you?
Cyber security road-mapping
Building a cyber security roadmap doesn’t need to be an arduous task, and the benefits of building a document – even a simple one – are enormous.
Start by listing out all the initiatives you could be doing. It helps to try and categorise each of these according to the role they might play in the NIST framework (Identify, Protect, Detect, Respond, Recover).
Create a simple document that has sections for each of the next 12 months. Then, plot one-time initiatives (such as the implementation of Application Control) followed by recurring activities (such as disaster recovery tests).
Finally – and here’s the secret to continuous cyber security – be sure to include a review of the roadmap every 6 months, and adjust it according to historical progress and future budget.
9. Compliance equals security
A widespread misconception in the realm of cybersecurity is that achieving compliance with industry regulations and standards automatically guarantees a secure environment.
While compliance is undoubtedly essential, it’s crucial to understand that it represents a baseline level of security, not an all-encompassing protection.
This is because cyber security frameworks are often designed to help businesses of certain types, end-customers or objectives.
For instance, frameworks like ISO 27001, the Information Security Manual or SCO2 contain an extensive collection of standards and best practices. These frameworks are typically expensive to comply with, and adopted by more mature organisations. By contrast, the Essential Eight is designed for all businesses and only focuses on a small number of highly effective strategies to minimise security risk.
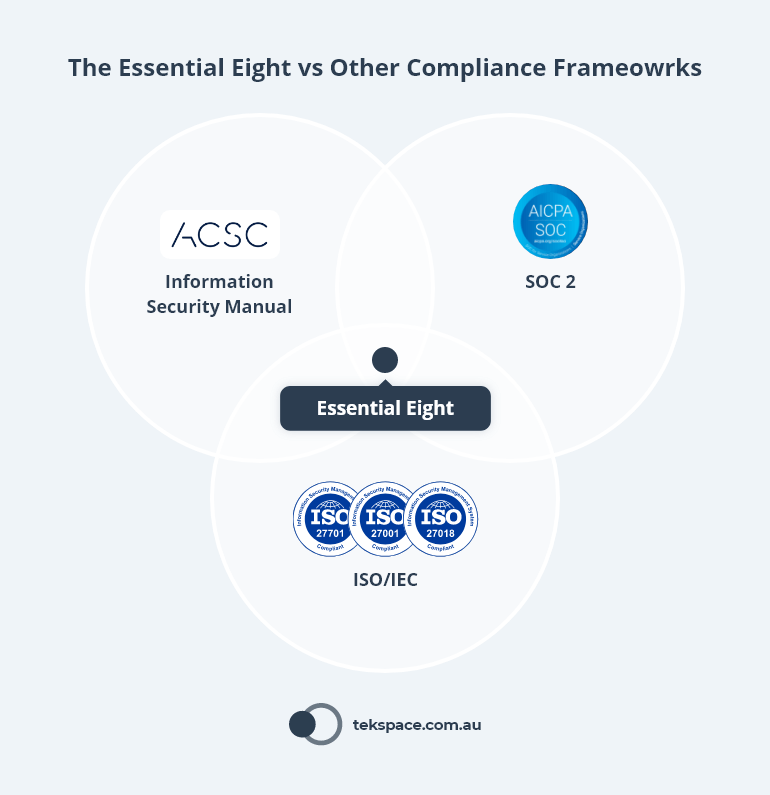
Rather than think of compliance as an end goal, organisations should view it as a starting point. Here are some additional steps to consider:
- Implement a risk-based approach: Assess the organisation’s specific risks and vulnerabilities, and tailor security measures to address these concerns, going beyond compliance requirements when necessary.
- Continuously monitor and update security measures: Stay informed about the latest threats and adapt security measures accordingly. Regularly review and update policies, procedures, and technologies to ensure they remain effective against evolving risks.
- Foster a security-aware culture: Foster a culture of cybersecurity awareness by providing ongoing training, promoting best practices, and emphasizing the importance of security at all levels of the organisation.
- Conduct regular security assessments: Perform periodic security assessments to identify potential vulnerabilities, measure the effectiveness of existing security measures, and implement improvements as needed.
Get more insights like these
Receive advice from our industry-leading cyber security experts.
Tekspace will never send you spam or share your email address with a third-party.

