Types of Phishing Simulations
Broadly speaking, all phishing simulations (regardless of their content) fall into one of three categories:
- Link Phishing Simulations
- Attachment Phishing Simulations
- Data Entry Phishing Simulations
Each category speaks to the goal of the phishing simulation, which gives insight into the unique susceptibility of an individual or the overarching vulnerability of a group.
For instance, the goal of a Link Phishing Simulation is to convince a user to click a link. Whereas the goal of a Data Entry Phishing Simulation is to convince a user to click a link, then enter data into a convincing landing page (such as a Microsoft 365 login page).
Failure Rate by Phishing Simulation Type
In 2021, more people fell for Attachment Phishing Simulations than Link or Data Entry Phishing Simulations.
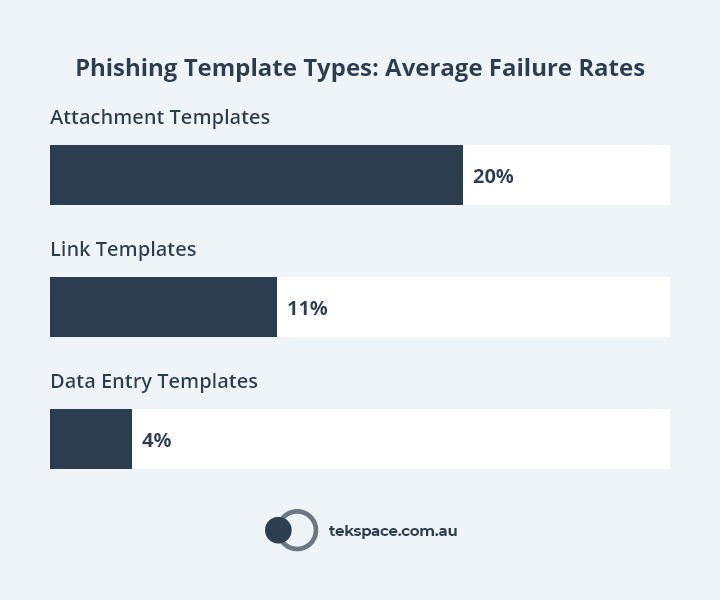
That said, these results must be taken with a grain of salt, because they reflect the average result of millions of phishing simulations sent to hundreds of organisations.
The results of a single organisation (or even individual) may vary greatly – influenced by factors such as industry, geography and even organisational culture.
When thinking about your own security awareness training program, it is important to consider your organisation in isolation of others.
Start by benchmarking all staff with the same phishing simulation template. Then, if you are manually building your own program, be sure to review the results of the group over time to schedule simulations and training that best suit the unique vulnerabilities of your team.
If you are using an automated platform, it should handle this tweaking and adjustment for each individual, according to their own susceptibility traits (such as topic, device, time of day, day of the week and so on).
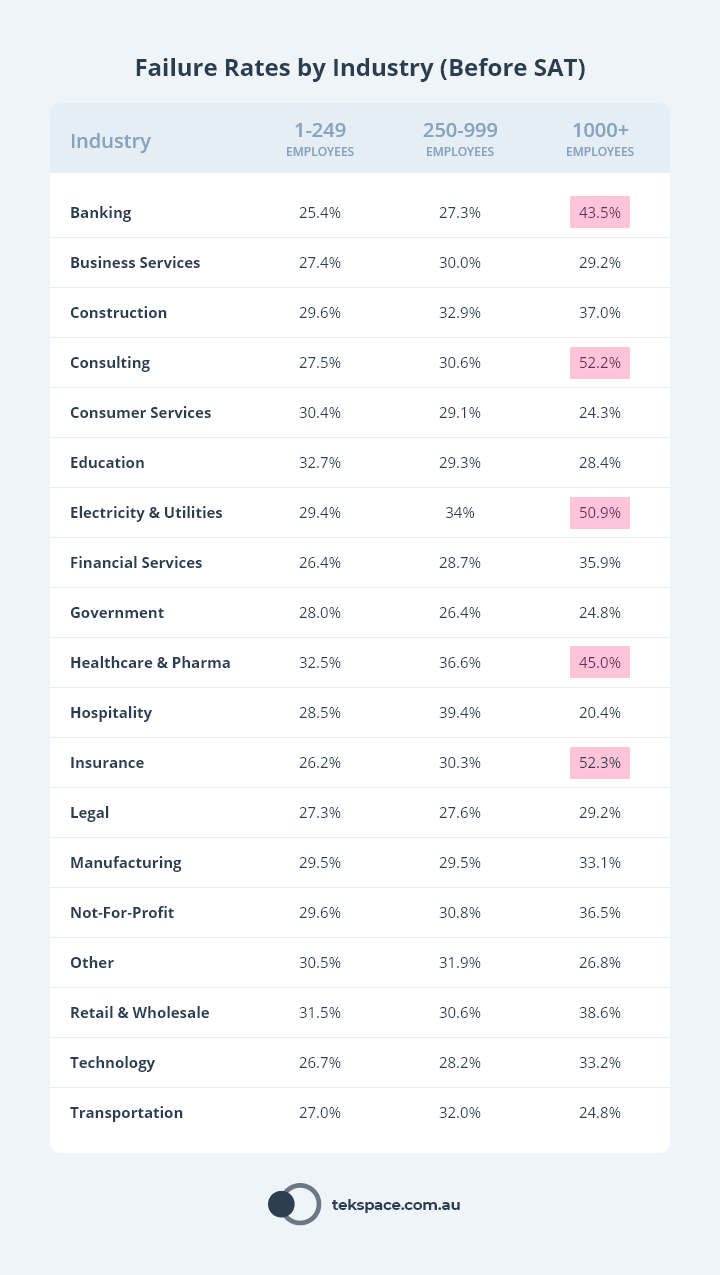
Failure Rate by Industry
A benchmark report produced in 2022 compared more than 30.1k organisations across numerous industries. Organisations were grouped by size:
- Small: 1 to 249 employees.
- Medium: 250 to 999 employees.
- Large: 1000+ employees.
To begin with, none of these organisations had any security awareness training program in place.
And of all organisations, the highest failure rates were observed in large organisations in the following industries:
- Insurance (52.3% failure rate).
- Consulting (52.2% failure rate).
- Energy and Utilities (50.9% failure rate).
- Healthcare and Pharmaceuticals (45% failure rate).
- Banking (43.5% failure rate).
After one year, the picture was much different. Average failure dropped significantly across all industries, from an average of 32.4% down to 5%.
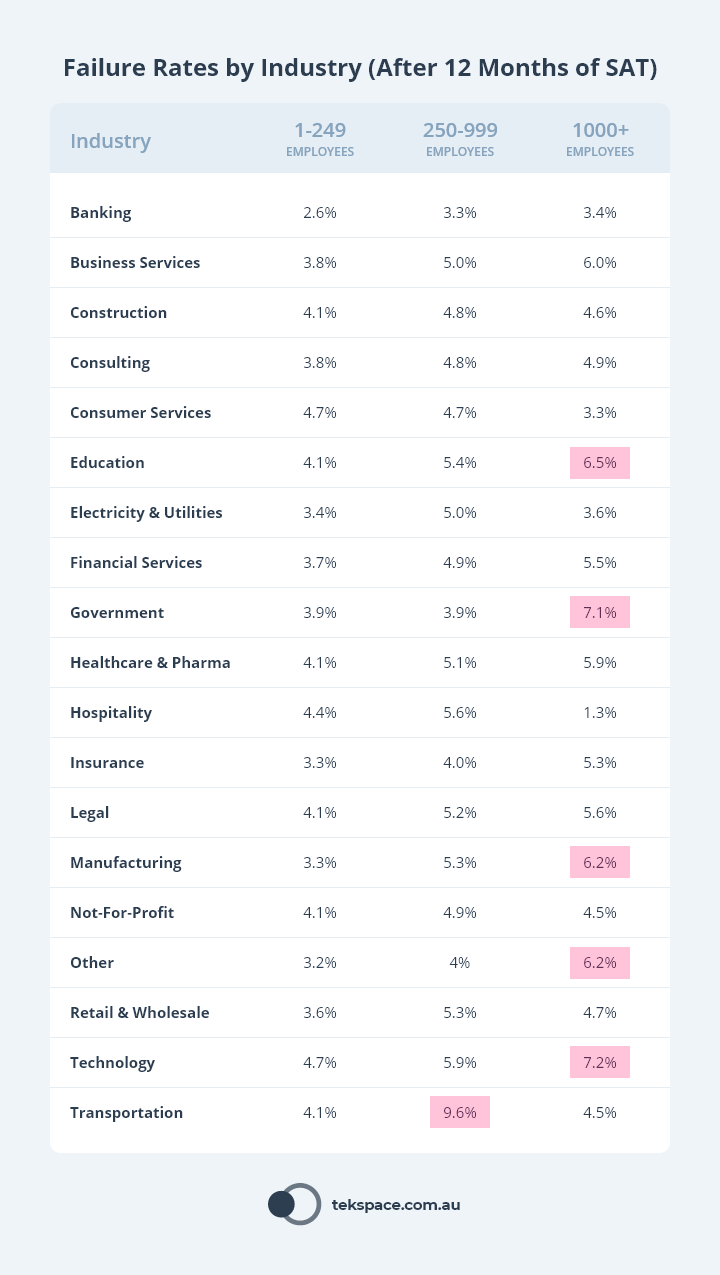
Results like these show the power and benefit of implementing organisation wide security awareness training.
They can also help you enrich your reporting by comparing your organisations’ results against those of your peers.
Phishing Susceptibility
Recent research from the University of Waterloo found there are three cognitive traits that moderate one’s susceptibility to phishing:
- Risk-taking Propensity: This is our inclination to take risks.
- Cognitive (Inhibitory) Control: This is our ability to control impulsive decisions.
- Social Cognition: This is the way we process, store and apply information about other people and social situations (source).
- Suspicion/Scepticism: This is a general attitude of doubt or questioning (source).
Of the three traits, Cognitive (Inhibitory) Control has the most direct impact on the susceptibility of an individual.
This is why ‘report phishing’ features are so valuable.
When staff are in the habit of reporting suspicious emails, they learn to be more sceptical of the emails they receive. They actively look for signs of phishing before compulsively (or even absentmindedly) clicking links, downloading attachments, or following nefarious directives (such as paying invoices to scammers).
Simulation Realism and Authenticity
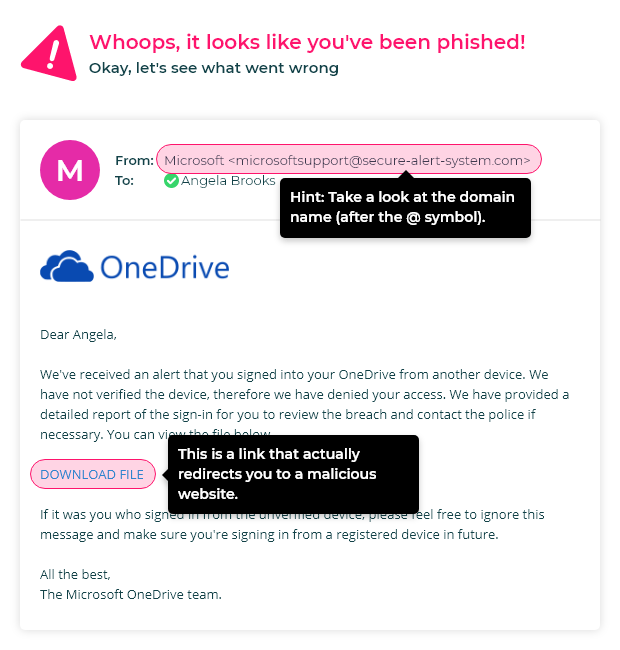
Oftentimes, the people responsible for implementing security awareness training programs like the idea of phishing simulation templates that accurately portray emails sent by well-known brands.
It is true that these simulation templates tend to have higher failure rates. In fact, we recently sent a hyper-realistic Spotify simulation to a client. 80% of staff opened the email, and 100% of staff who opened the email clicked the link.
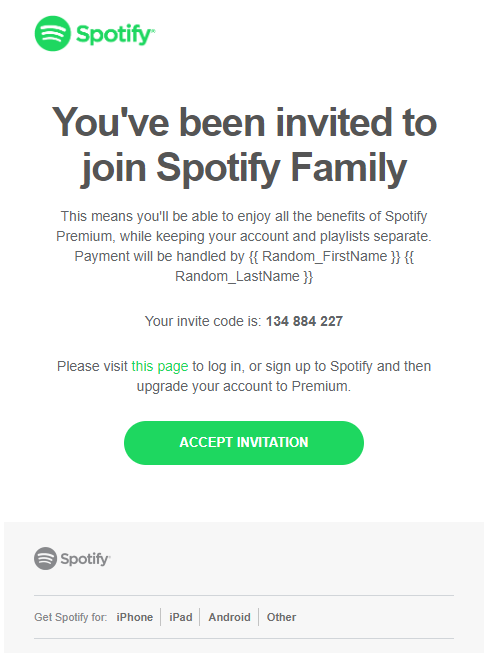
However, not all simulations need to accurately represent a well-known brand to be authentic and trip up employees.
In fact, research shows that 9 of the top 10 trickiest phishing simulations are simple text-based emails from HR that address company policies (such as changes to dress code, holiday leave, bonuses, social media and code of conduct breaches).
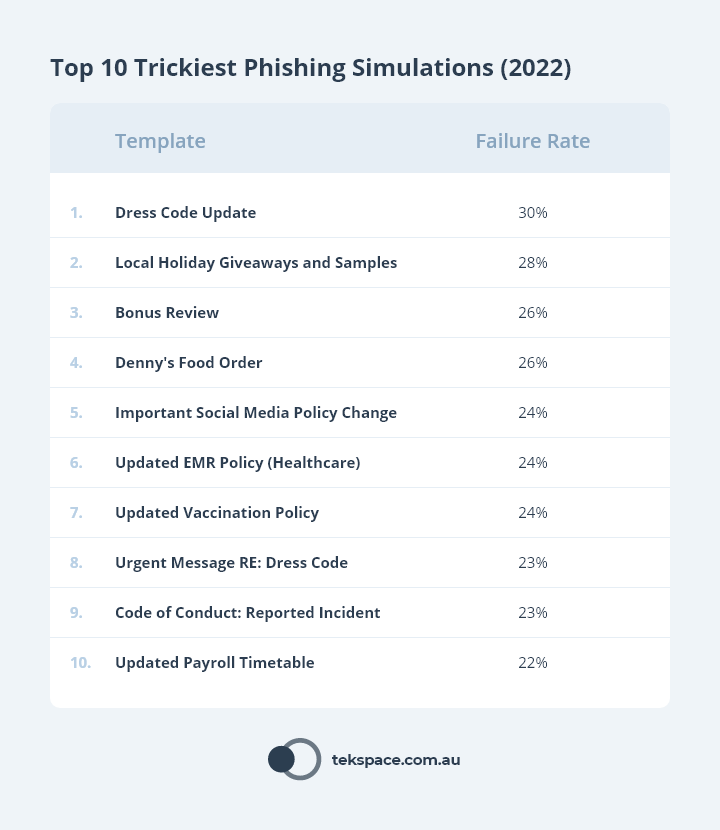
With this in mind, ‘realistic simulations’ are not just beautifully branded emails, but any email that a staff member is likely to take seriously and engage with.
So, your phishing simulation library should include emails that look like they come from the big brands (especially gift card offers), but it should also include those ‘company policy’ type emails.
Note: There’s some nuance here. Most people aren’t going to have advanced phishing detection skills, especially in the first 4 to 8 months of your program. So as much as hyper-realistic simulations are important, it’s okay (and ideal) to have simulations that are more obviously fake. This empowers people who aren’t as skilled because they get the psychological benefits of positive reinforcement when they successfully identify a phishing simulation. Sending simulations that match each person’s capability level is easy if you use an AI-driven security awareness training platform.
Business Email Compromise and Spear Phishing
Business Email Compromise (BEC, or “Spear Phishing”) is where an attacker targets a specific person, rather than a group.
In BEC attack, the scammer impersonates a trusted another person or entity (such as a colleague, client, or key supplier), often by sending the target an email from a fake or compromised email address.
Did you know that in 2021, 79% of organisations (globally) experienced BEC attacks. Why? Because they work.
The APWG Phishing Activity Trends Report for Q1 2022 shows that gift card requests made up 63% of all BEC attacks, followed by payroll diversion attempts (16%) and wire transfer schemes (9%). The remaining 12% was made up of miscellaneous methods.
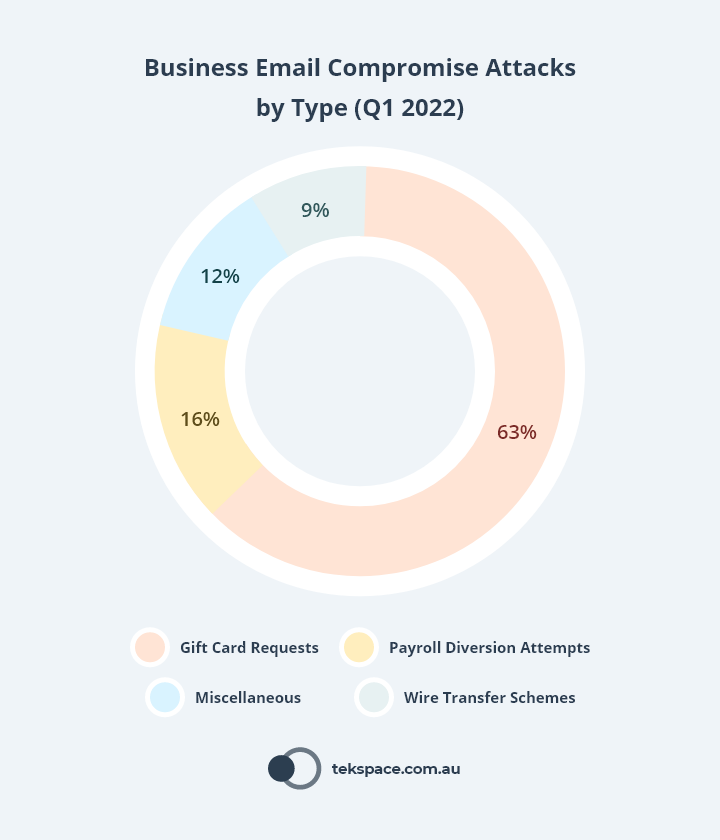
So how do you give staff the knowledge to identify spear phishing emails before they do harm? By building them into your security awareness training program.
Modern and sophisticated security awareness training platforms offer the ability to upload your company email signature and autonomously send spear phishing simulations from one person to another.
They can even use the department that a person belongs to (such as Finance or HR) to send highly relevant and believable spear phishing emails. For example, a spear phishing email might be sent from an employee in Finance requesting the review of an invoice, or a spear phishing email from an employee in Marketing requesting the approval of a budget.
But protection against spear phishing requires more than having a security awareness program in place.
Internal processes should be established to ensure every request for a transfer of money is verified by more than one person before the transfer is executed. Part of the verification process should happen outside of email, to circumvent mailboxes that have been compromised.
Dynamic Phishing Simulation Difficulty
Until recently, most security awareness training platforms worked by sending the same emails to all staff. While this is useful for benchmarking groups of people, it doesn’t help to drive long term engagement.
This approach disengages people who are proficient at identifying phishing emails, because they see through the tactics and are less likely to see the value in the program.
It also disengages people who are particularly vulnerable because their experience of the program is one of continuous failure with no positive re-enforcement.
To drive engagement, sophisticated security awareness training platforms are now using artificial intelligence and machine learning to:
- Continuously assess the susceptibility profile of each person; then
- Send phishing simulations (and training) that is uniquely adapted to their strengths and weaknesses.
For example, the program we offer our clients can accurately identify the days of the week, time of the day, device and even the topics that catch each person the most.